#2 ISO 27001: ISO 27001 and the Essential Eight
Strengthening Your Cybersecurity Foundation
ISO 27001WHAT IS ISO 27001DAY 1
Canzuki Admin
1/30/20253 min read


#2 - ISO 27001:ISO 27001 and the Essential Eight
Strengthening Your Cybersecurity Foundation
In the first article of this series, I introduced ISO 27001 as a powerful framework for developing a robust Information Security Management System (ISMS). But let's be honest, it can feel overwhelming. Where do you even begin? If you've already taken steps to implement the Australian Cyber Security Centre's (ACSC) Essential Eight, you're not just starting from scratch - you've already laid a strong foundation. In this article, I'll show you how the Essential Eight provides key building blocks for ISO 27001, and how, together, they can transform your cybersecurity.
Recap: The Essential Eight
The Essential Eight is a set of prioritised mitigation strategies designed to protect your systems against a range of cyber threats. You can think of them as the foundational controls, the "must-haves" for any Australian business. They are:
Application Control: Preventing the execution of unapproved or malicious programs.
Patch Applications: Updating applications with the latest security patches.
Configure Microsoft Office Macro Settings: Blocking or restricting the use of potentially harmful macros.
User Application Hardening: Removing or disabling unnecessary features in applications.
Restrict Administrative Privileges: Limiting the number of users with administrative access.
Patch Operating Systems: Keeping operating systems up-to-date with the latest security patches.
Multi-Factor Authentication: Requiring multiple forms of authentication to verify user identities.
Regular Backups: Ensuring that important data is backed up regularly and can be restored.
The Essential Eight as a Stepping Stone to ISO 27001
Implementing the Essential Eight is a fantastic starting point for any business looking to improve its cybersecurity. But it's important to understand that the Essential Eight is not a complete security solution. It’s more like the foundation of a house - essential, but you need to build upon it to create a secure and resilient structure.
This is where ISO 27001 comes in. It provides a comprehensive framework that encompasses the Essential Eight and much more. ISO 27001 helps you build a complete ISMS, addressing not only technical controls but also policies, processes, and people.
Mapping the Essential Eight to ISO 27001's Annex A Controls
Many of the Essential Eight mitigation strategies align directly with specific controls within ISO 27001's Annex A. Here's a glimpse of how they map:
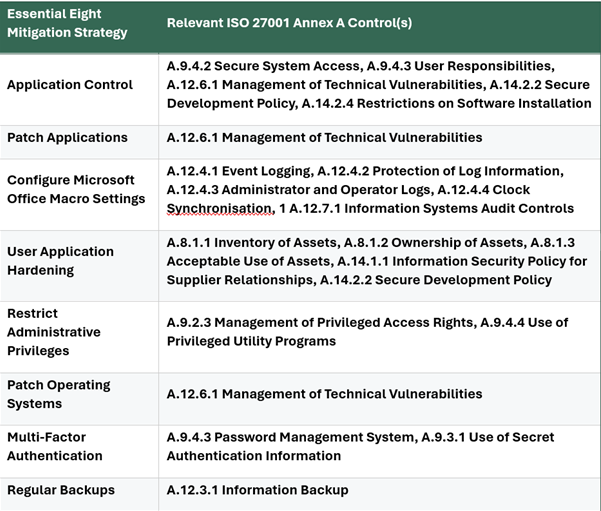
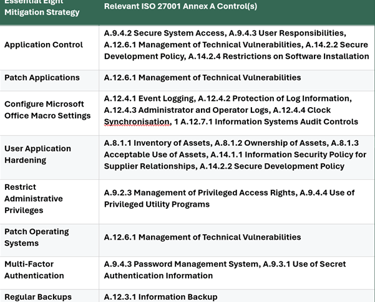
Beyond the Essential Eight: The Broader Scope of ISO 27001
While the Essential Eight provides a strong starting point, ISO 27001 takes you further. It helps you:
Establish a formal ISMS: This includes defining your security policy, objectives, and scope.
Conduct a comprehensive risk assessment: Identify, analyse, and evaluate risks beyond the scope of the Essential Eight.
Develop and implement a risk treatment plan: Address risks in a structured and consistent manner.
Create security policies and procedures: Document your security practices and ensure they are followed.
Implement a wider range of security controls: Address areas not covered by the Essential Eight, such as physical security, cryptography, and supplier security.
Monitor, review, and improve your ISMS: Ensure your security posture remains effective over time.
Train and raise awareness amongst staff: Annex A includes controls relating to HR Security.
Canzuki: Helping You Build on a Strong Foundation
At Canzuki, we understand that implementing ISO 27001 can seem like a big step. But if you've already embraced the Essential Eight, you're well on your way. We can help you leverage that foundation to achieve full ISO 27001 compliance and build a truly resilient security posture.
The Essential Eight and ISO 27001 are not competing frameworks but rather complementary approaches to cybersecurity. The Essential Eight provides a strong foundation, while ISO 27001 offers a comprehensive framework for building and maintaining a robust ISMS. Combining the two can significantly enhance your security posture and protect your business from the ever-evolving cyber threat landscape.
In my next article, I'll cover the essentials of risk assessment and how to develop strategies to reduce those risks, Stay tuned!
Tired of worrying about your cybersecurity vulnerabilities? Let's change that! Contact Canzuki for a free consultation and discover how ISO 27001 can bring you greater peace of mind.
Call us at +61 2 7227 9388 or email hello@canzuki.com
Contact
Auckland
+64 9 871 4471
Sydney
+61 2 7227 9388
hello@canzuki.com
Connect
Services
Observability Solutions
Contact Center Technology
Voice Infrastructure
Consulting Services
Canzuki
Customer Experience consulting specializing in contact center technology and telecommunications solutions.
